Content security is not only about CAS or DRM software security. It’s a combination of different security and anti-piracy features that work together as a set of solutions to provide a more holistic approach against piracy. Read this blog to learn how we can protect your content and service beyond traditional software security.
Software security is all around us, like in the lyrics of that famous song, you can feel it in your fingers when you use your smart phone, or controlling your Android TV set-top-box with your remote control, it’s digitally written in the wind with even Free-To-Air operators relying on it to protect their OTT Services; it’s literally everywhere you go, and it has even overtaken smartcard based security – the previously de-facto solution of the pay-tv industry.
But is it not a bit paradoxical to use a known weaker security, considering the significant growth of streaming and of course piracy over the last couple of years? In our recent eBook on PVOD, we highlighted that more than 80% of piracy is attributable to streaming, with the total piracy revenue of illegal IPTV subscription in the US being more than 1B$. How then, can software be at the heart of device security? Ultimately, it might use mathematical and cryptographic wonders to hide its implementation, be protected through a secure enclave, a trusted environment, you name it; but in the end it is running software, and software will always be vulnerable. Last year for example, multiple and repeated attacks have allowed hackers to extract content from almost all popular streaming services such as Netflix, Disney+, HBO or Amazon, and all this using basic publicly available tools.
And yet software security usage across devices keeps growing…
The reality is that content security is not only about CAS or DRM Software security. It’s a combination of different security and anti-piracy features that work together as a set of solutions to provide a more holistic approach against piracy. While of course hardware security is the most secure, especially for premium content as the investment is typically higher, it’s naturally more immune to common attacks than a standard software solution. However, content value is not the only variable affecting exposure to pirates– particularly if the content is only available on open devices or through web browsers.
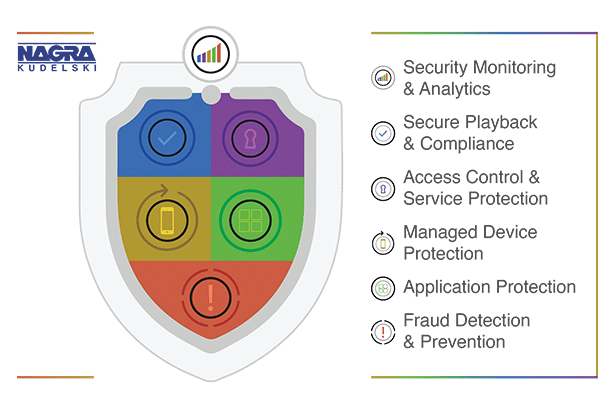
Take for example device tampering, content redistribution or password sharing; these are just some examples that are hard to solve using hardware security, and that’s why we as an industry need to embrace the world beyond the traditional security boundaries. At NAGRA we continue to offer unparalleled hardware security solutions for both Live TV and OTT but we’re also particularly excited about the latest upgrades to our Active Streaming Protection framework that provides multiple industry proven technologies; from secure playback and application protection to device protection and fraud prevention – all working together to address content and service piracy threats.
So based on this, is choosing software security a risk? The answer lies in the definition of the service’s security strategy. While hardware security has a clear role for secure playback, so does choosing a more modular and flexible set of security solutions that can be deployed and enabled at a time relevant to the operator’s business. This provides a winning approach with which to tackle today’s challenges of securing both the content and the service. The approach also offers a level of business robustness that standard software security in the form of multi-DRM just cannot offer or compete with.
How are you protecting your content and is it fit for purpose against your business ambition? We’d love to continue the conversation so get in touch with us here or check out the latest in content and service protection provided by NAGRA Active Streaming Protection.